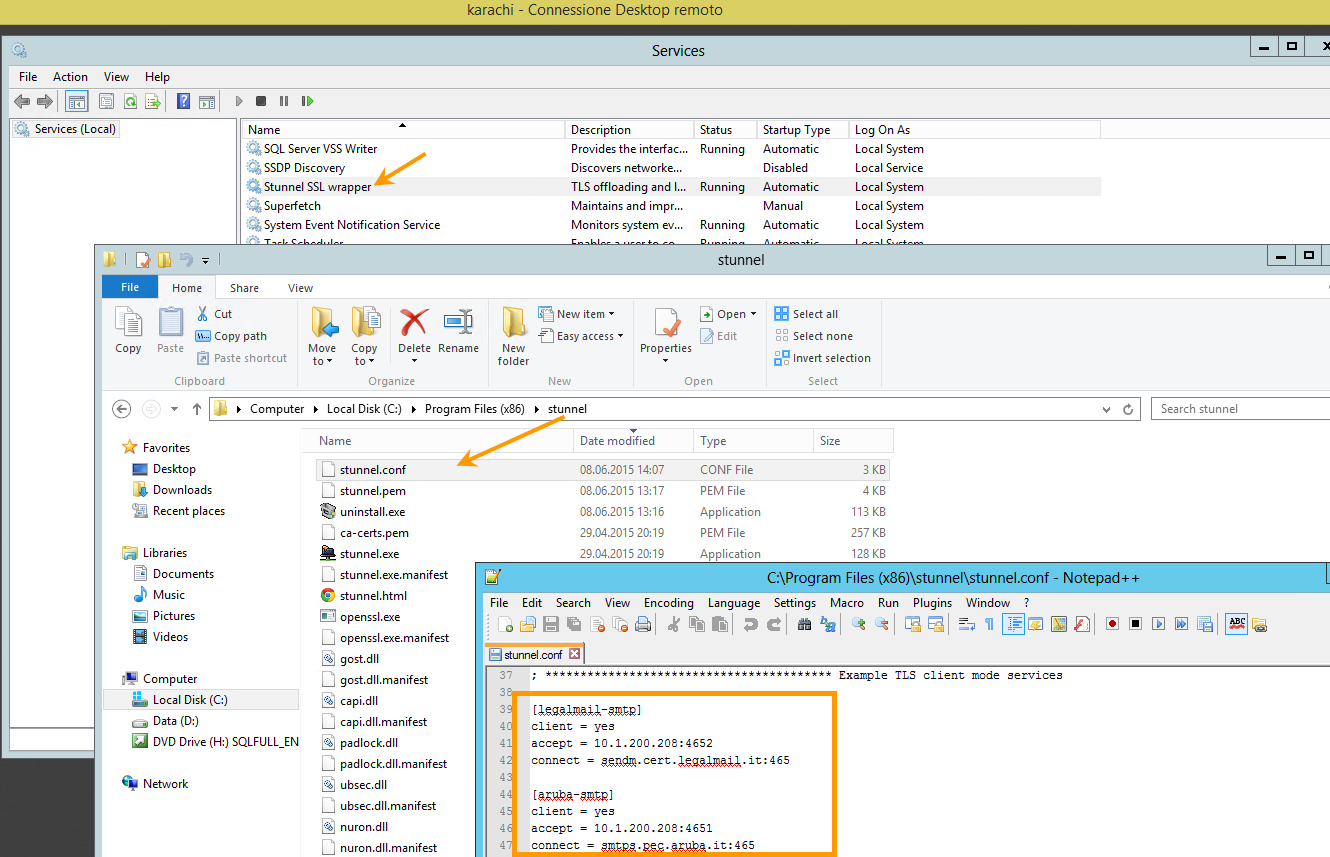
Configurazione STUNNEL
;
Sample stunnel configuration file for Win32 by Michal Trojnara 2002-2015
; Some options used here may be inadequate for your particular
configuration
; This sample file does *not* represent stunnel.conf defaults
; Please consult the manual for detailed description of available options
;
**************************************************************************
; * Global options
*
;
**************************************************************************
; Debugging stuff (may be useful for troubleshooting)
;debug = info
;output = stunnel.log
; Enable FIPS 140-2 mode if needed for compliance
;fips = yes
; Microsoft CryptoAPI engine allows for authentication with private keys
; stored in the Windows certificate store
; Each section using this feature also needs the "engineId = capi" option
;engine = capi
;
**************************************************************************
; * Service defaults may also be specified in individual service sections
*
;
**************************************************************************
; Enable support for the insecure SSLv3 protocol
;options = -NO_SSLv3
; These options provide additional security at some performance
degradation
;options = SINGLE_ECDH_USE
;options = SINGLE_DH_USE
;
**************************************************************************
; * Service definitions (at least one service has to be defined)
*
;
**************************************************************************
; ***************************************** Example TLS client mode
services
;****ACCEPT= LOCALSERVER(KARACHI) :PORT
[legalmail-smtp]
client = yes
accept = 10.1.200.208:4652
connect = sendm.cert.legalmail.it:465
[aruba-smtp]
client = yes
accept = 10.1.200.208:4651
connect = smtps.pec.aruba.it:465
; Encrypted HTTP proxy authenticated with a client certificate
; located in the Windows certificate store
;[example-proxy]
;client = yes
;accept = 127.0.0.1:8080
;connect = example.com:8443
;engineId = capi
; ***************************************** Example TLS server mode
services
;[pop3s]
;accept = 995
;connect = 110
;cert = stunnel.pem
;[imaps]
;accept = 993
;connect = 143
;cert = stunnel.pem
;[ssmtp]
;accept = 465
;connect = 25
;cert = stunnel.pem
; TLS front-end to a web server
;[https]
;accept = 443
;connect = 80
;cert = stunnel.pem
; "TIMEOUTclose = 0" is a workaround for a design flaw in Microsoft
SChannel
; Microsoft implementations do not use TLS close-notify alert and thus
they
; are vulnerable to truncation attacks
;TIMEOUTclose = 0
; Remote cmd.exe protected with PSK-authenticated TLS
; Create "secrets.txt" containing IDENTITY:KEY pairs
;[cmd]
;accept = 1337
;exec = c:\windows\system32\cmd.exe
;execArgs = cmd.exe
;PSKsecrets = secrets.txt
; vim:ft=dosini
Esempio di configurazione Stunnel su Karachi per LegalMail e Aruba:
Appendice A: PEC STATUS-Elenco stati PEC






